- Citations
- A. K. Abasi, M. Aloqaily, M. Guizani, and B. Ouni, Metaheuristic Algorithms for Securing 6G Wireless Communications: Recent Advances and
Applications, ACM Computing Surveys, 2023.
DOI:N.B submitted
Source Code:-
PDF Download:Upcoming








The increasing number of applications and devices in the Sixth-generation (6G) networks and the diversity of mobile data, architectures, and technologies make security and privacy a critical concern. Advanced metaheuristics algorithms (MHAs) have recently become a viable solution for optimizing security and privacy in wireless networks, combining game theory and convex optimization, and several other advanced models. As a subfield of Artificial Intelligence (AI), MHAs are inspired by concepts from Evolutionary Algorithms (EAs), Trajectory-based Algorithms (TAs), and Swarm Intelligence (SI). Recent implementations of MHAs in the 6G networks have effectively solved complex security and privacy problems.
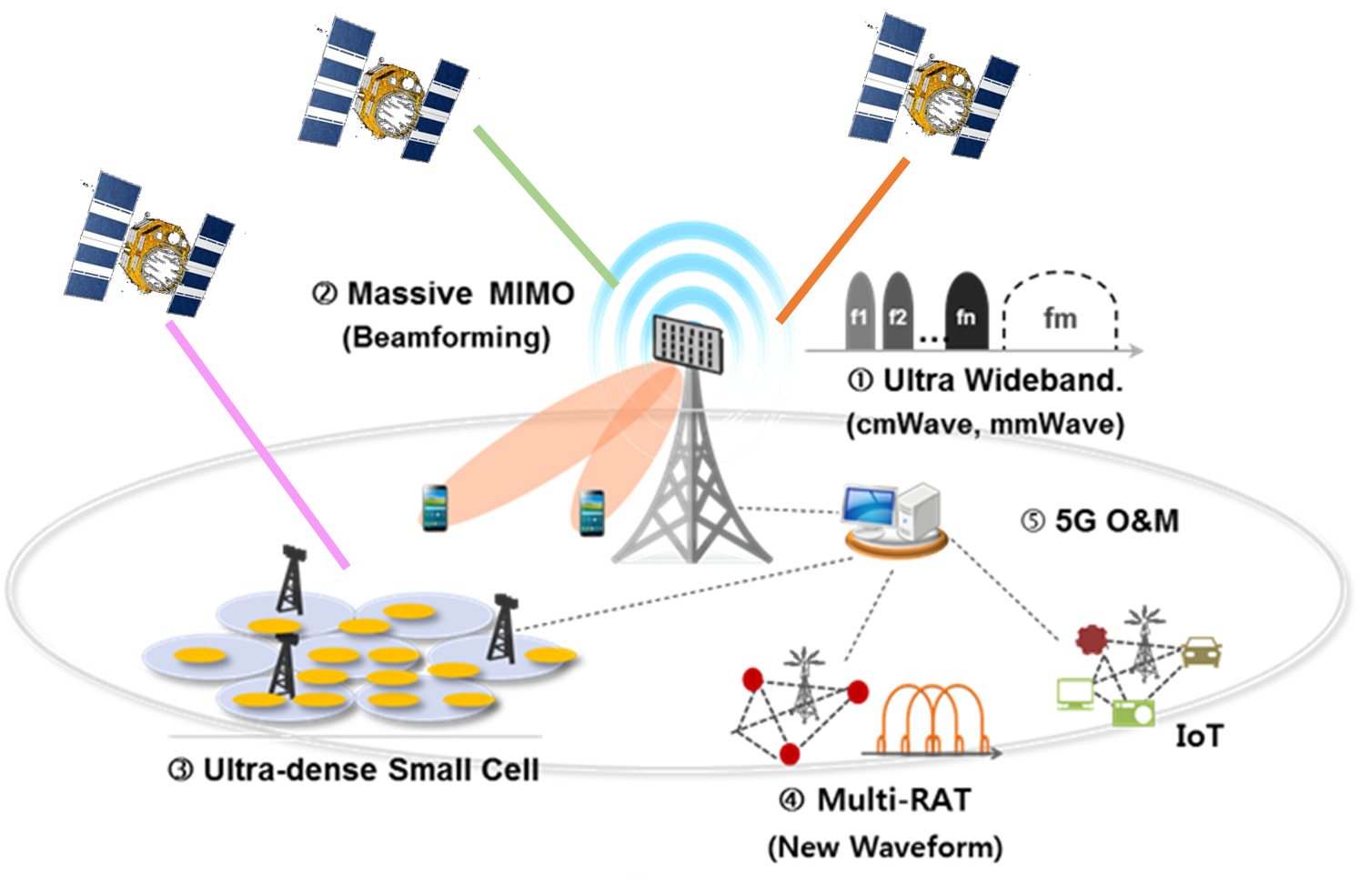
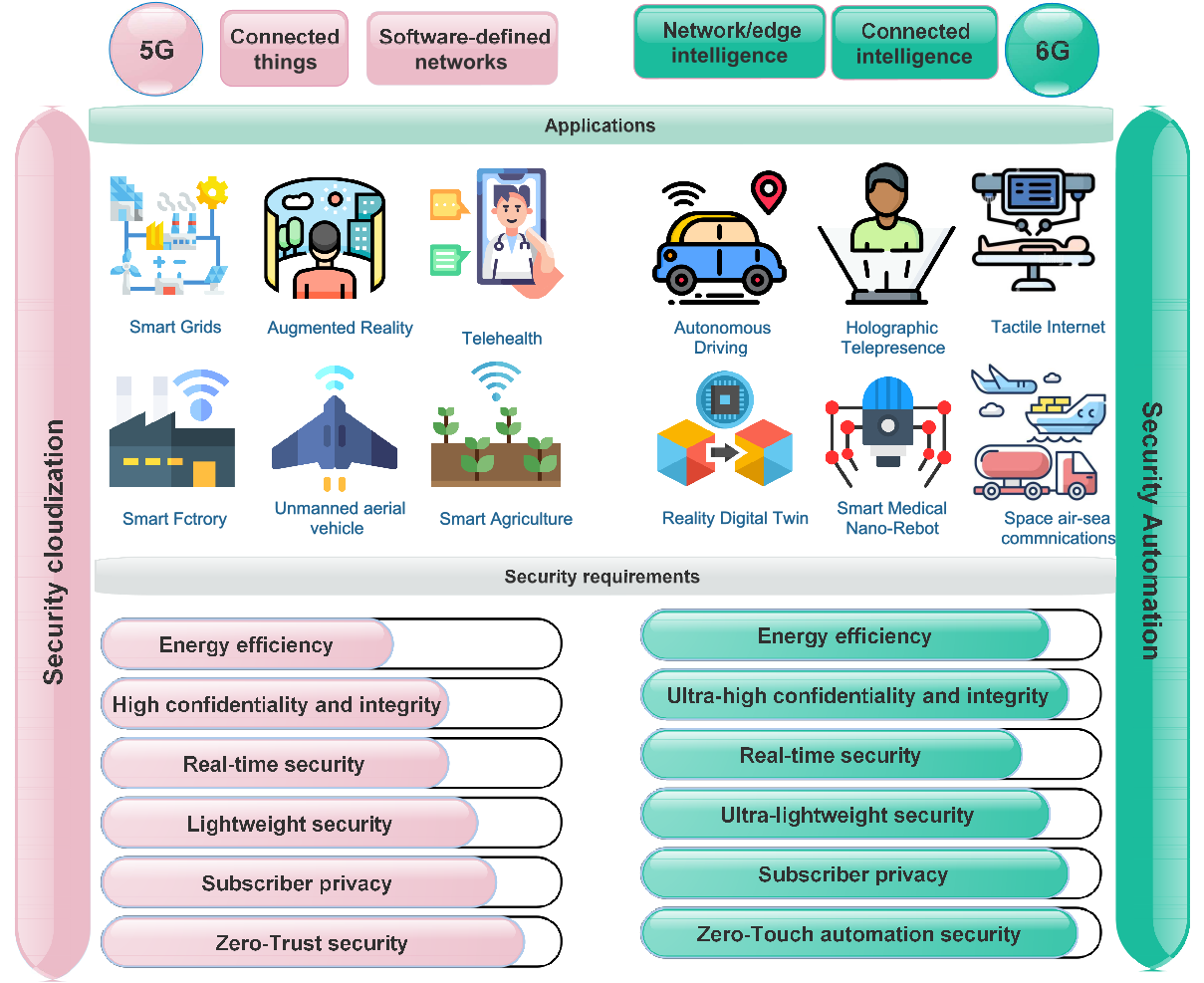
This project aims to improve wireless networks' security and privacy by utilizing advanced metaheuristic algorithms. The project aims to achieve several objectives, including developing optimization frameworks for enhancing network performance and reducing security risks, developing robust models that can adapt to various attacks while maintaining accuracy. Additionally, the project seeks to optimize network parameters using hybrid metaheuristic algorithms, such as Particle Swarm Optimization (PSO) or Multi-Verse Optimizer (MVO), to improve network security and efficiency. The proposed methods will be evaluated through extensive simulations to assess their effectiveness in improving network security and robustness against adversarial attacks. The results of this project will contribute to developing more secure and efficient wireless networks in various fields, such as telecommunications, healthcare, and transportation.
Metaheuristic algorithms offer a flexible and efficient approach to solving complex optimization problems in wireless networks. They are inspired by concepts from various fields, such as Evolutionary Algorithms (EAs), Trajectory-based Algorithms (TAs), and Swarm Intelligence (SI), and have been successfully implemented in various wireless network scenarios. By using metaheuristic algorithms, it is possible to optimize security and privacy in wireless networks more effectively than traditional optimization methods.
Optimization frameworks and trust score adaptation are two methods used to enhance security and privacy in wireless networks using metaheuristic algorithms. Optimization frameworks, such as the one proposed in this project for Deep Learning (DL) hyperparameters in 6G millimeter-wave (mmWave) networks, optimize network performance through intelligent selection of network parameters. Trust score adaptation, such as the method proposed in this project for reducing the security risk of Fast Gradient Sign Method (FGSM) attacks in Federated Learning (FL), adjusts the trust scores of clients to prevent malicious attacks and maintain network integrity. These methods are optimized using metaheuristic algorithms, enhancing wireless networks' security and privacy.